AI-Powered Deception: A Growing Threat to Society, Cisco Confirms Chinese Cyber Attack Targeting U.S. Telecom, Best Practices for Hardened Container Management and more
Latest News – SunsetHost – February 21, 2025
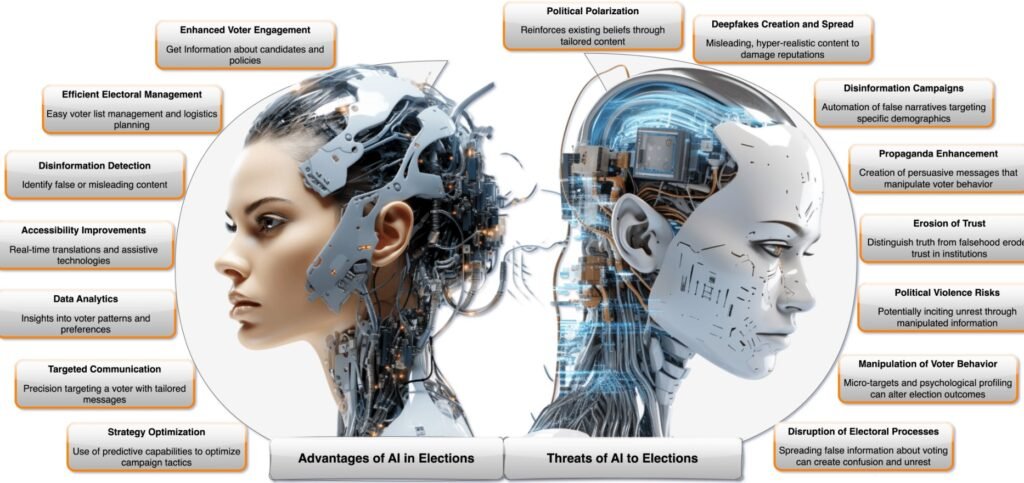
AI-Powered Deception: A Growing Threat to Society With the rapid advancements in artificial intelligence, the risk of AI being weaponized for deception and manipulation has escalated. Propaganda has always played a role in conflict, and AI technologies are amplifying this danger. From deepfakes to automated misinformation campaigns, AI-powered tools are posing a significant challenge to societal stability. The issue dates back as far as 515 BC, where the Persian King Darius used written inscriptions to control narratives, drawing parallels to modern AI’s potential for influence.
Cisco Confirms Chinese Cyber Attack Targeting U.S. Telecom Cisco has confirmed that a Chinese cyber-espionage group, Salt Typhoon, used a known security vulnerability (CVE-2018-0171) to compromise U.S. telecom networks. The group exploited the flaw and obtained login credentials, marking another significant breach in global cybersecurity efforts. The attack underscores the importance of patching outdated vulnerabilities and securing sensitive communications infrastructure.
Best Practices for Hardened Container Management Containers are a popular method for deploying software, but they can introduce security risks. A newly released guide outlines proven best practices for hardened container management to ensure systems remain secure while benefiting from faster deployment cycles. The guide emphasizes proactive security measures to avoid the exploitation of vulnerabilities that containers can sometimes introduce.
CISA Flags Critical Craft CMS Vulnerability The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has added a critical vulnerability (CVE-2025-23209) in Craft CMS to its Known Exploited Vulnerabilities catalog. Active attacks are already underway, exploiting the flaw, which affects many web applications. Websites using this content management system are advised to apply patches immediately to mitigate the risk.
North Korean Hackers Target Freelance Developers with Malware North Korean hackers are using fake job offers to target freelance software developers, aiming to infect their systems with malware like BeaverTail and InvisibleFerret. These malware families are designed to work across platforms, and the attackers’ goal is to gain unauthorized access to the developer’s systems. This ongoing campaign highlights the risks of phishing and social engineering tactics targeting remote workers.
China-Linked Attackers Exploit Check Point Flaw for Ransomware A new China-linked cyberattack cluster has been discovered, exploiting a vulnerability in Check Point products to deploy malicious software, including ShadowPad and ransomware. The attacks primarily target European healthcare organizations. These intrusions involve sophisticated techniques, with a focus on obtaining sensitive data for ransomware deployment.
PCI DSS 4.0 Mandates DMARC by March 31, 2025 As part of its ongoing efforts to enhance payment card security, PCI DSS has mandated that businesses handling cardholder data must implement DMARC (Domain-based Message Authentication, Reporting & Conformance) by March 31, 2025. This policy aims to combat email spoofing and phishing attacks that can undermine trust in payment systems.
Cybercriminals Use Eclipse Jarsigner to Distribute XLoader Malware A new malware campaign has been observed using Eclipse Jarsigner to distribute the XLoader malware via ZIP archives. This technique leverages a legitimate application associated with the Eclipse Foundation to bypass security measures. The campaign is yet another reminder of how cybercriminals exploit trusted tools to deliver malware unnoticed.
For detailed information and guidance on each of these stories, check out the full articles on SunsetHost’s website.
Recent Posts
- Advanced Malware, AI-Driven Attacks, and Critical Platform Vulnerabilities Redefine the 2026 Threat Landscape
- SunsetHost Tech & Cybersecurity Report: Holiday Hosting Deals and Critical Threat Alerts
- Semi-Dedicated Hosting Steps Into the Spotlight: SunsetHost’s Deep Dive Into Performance, Pricing, and What Tech Users Need to Know
- SunsetHost Hacker News & Tech Report — KVM VPS Hosting Deep Dive + Today’s Biggest Cyber & AI Security Stories
- SunsetHost Hacker News & Tech Report: OpenVZ VPS Hosting Steps Up as Developers Demand More Power, More Control, and More Transparency
Recent Comments
Categories
